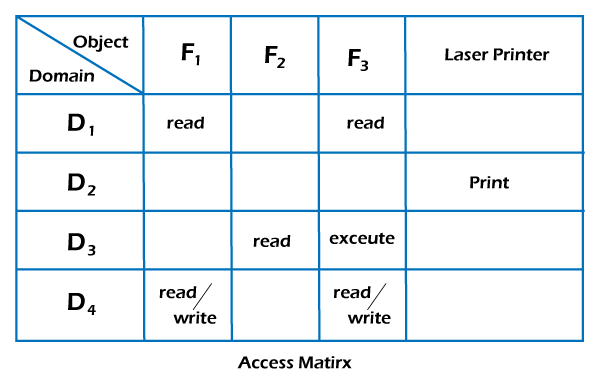
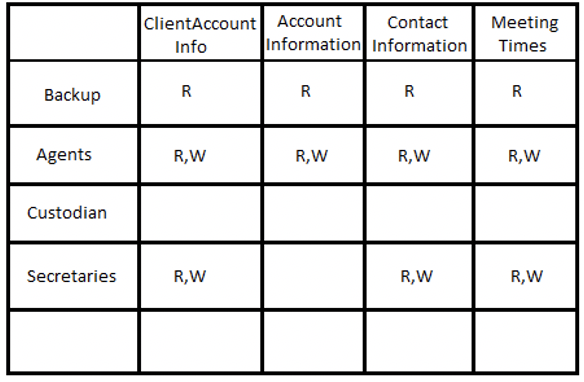
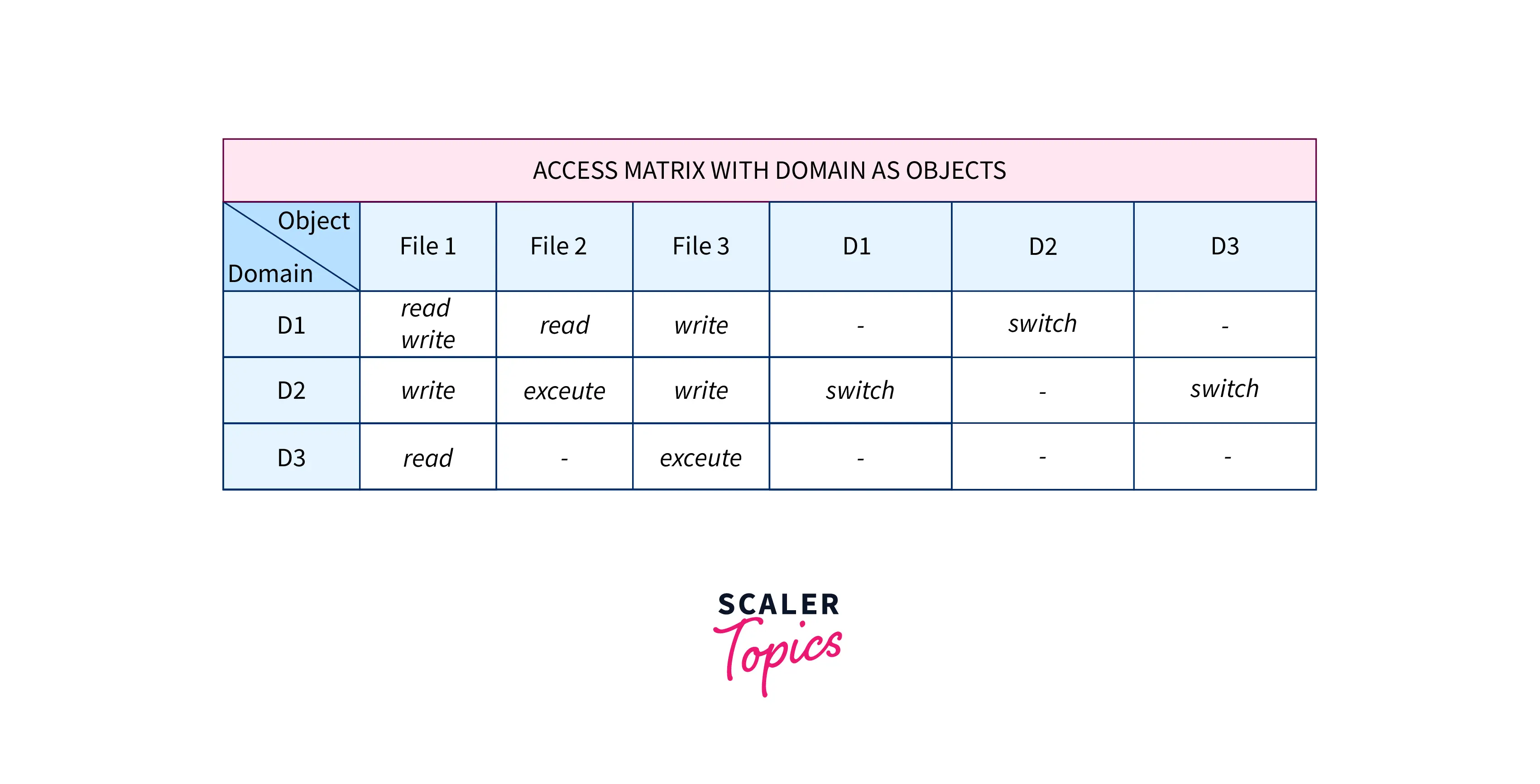
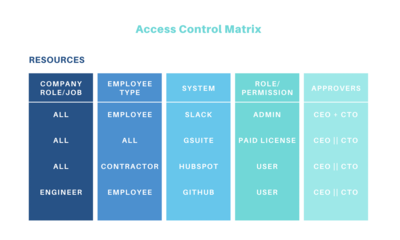
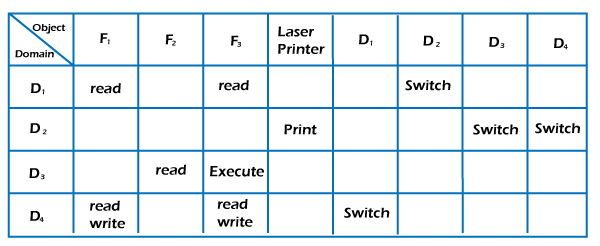
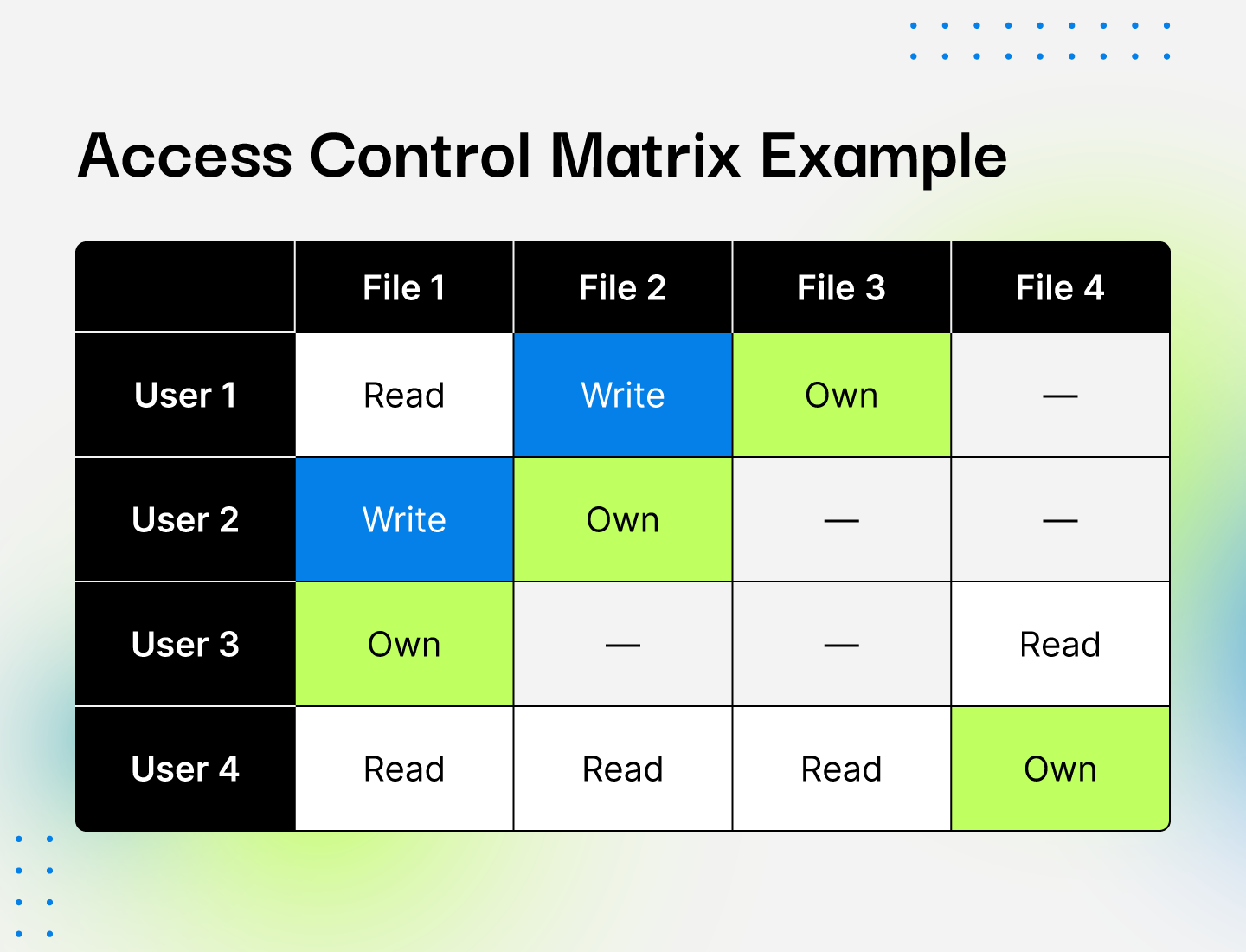
1. An access control matrix, and its access control list and capability... | Download Scientific Diagram
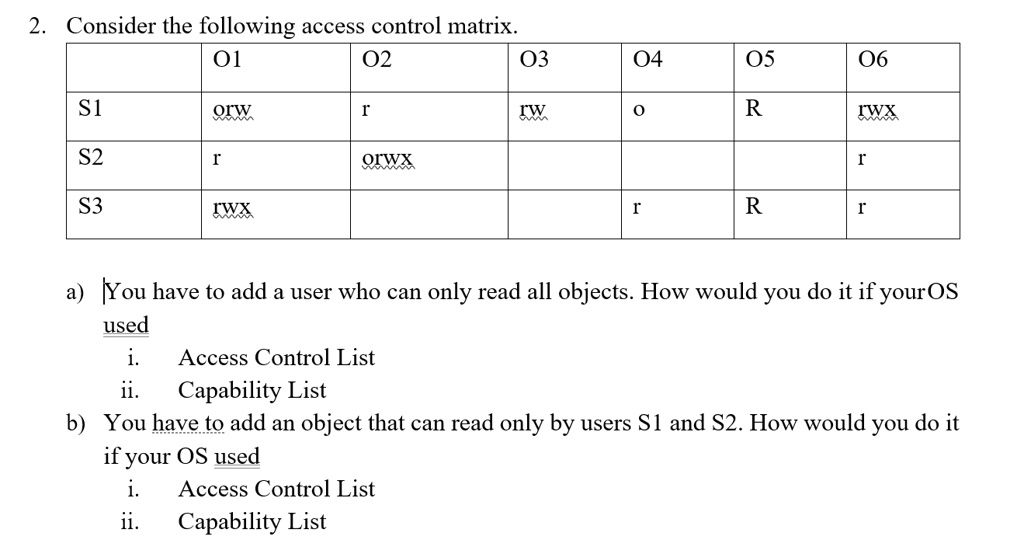
SOLVED: Consider the following access control matrix: | | 01 | 02 | 03 | 04 | 05 | 06 | |—|—–|——|——|——|——|——| | s1| orw | r | rw | 0
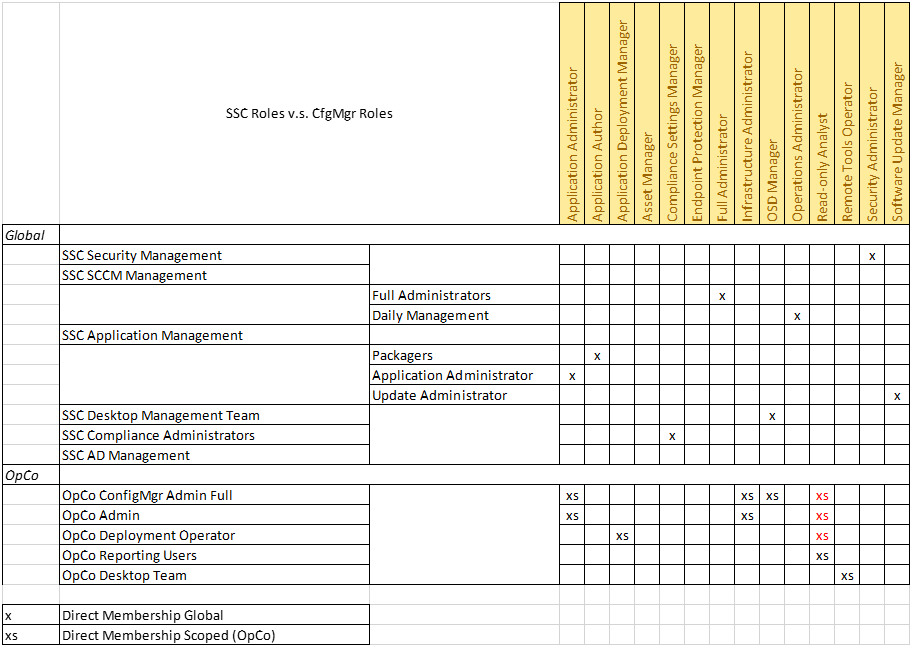
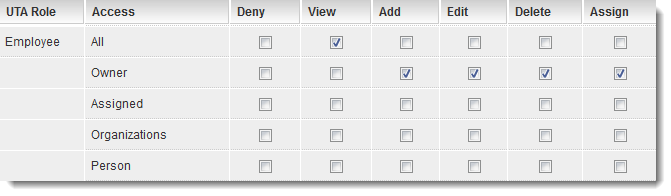
Role Based Access Control in ConfigMgr 2012: Part 3 Mapping OpCo roles to ConfigMgr roles - Modern Workplace Blog

To improve the current security model and efficiency in cloud computing using access control matrix | Semantic Scholar