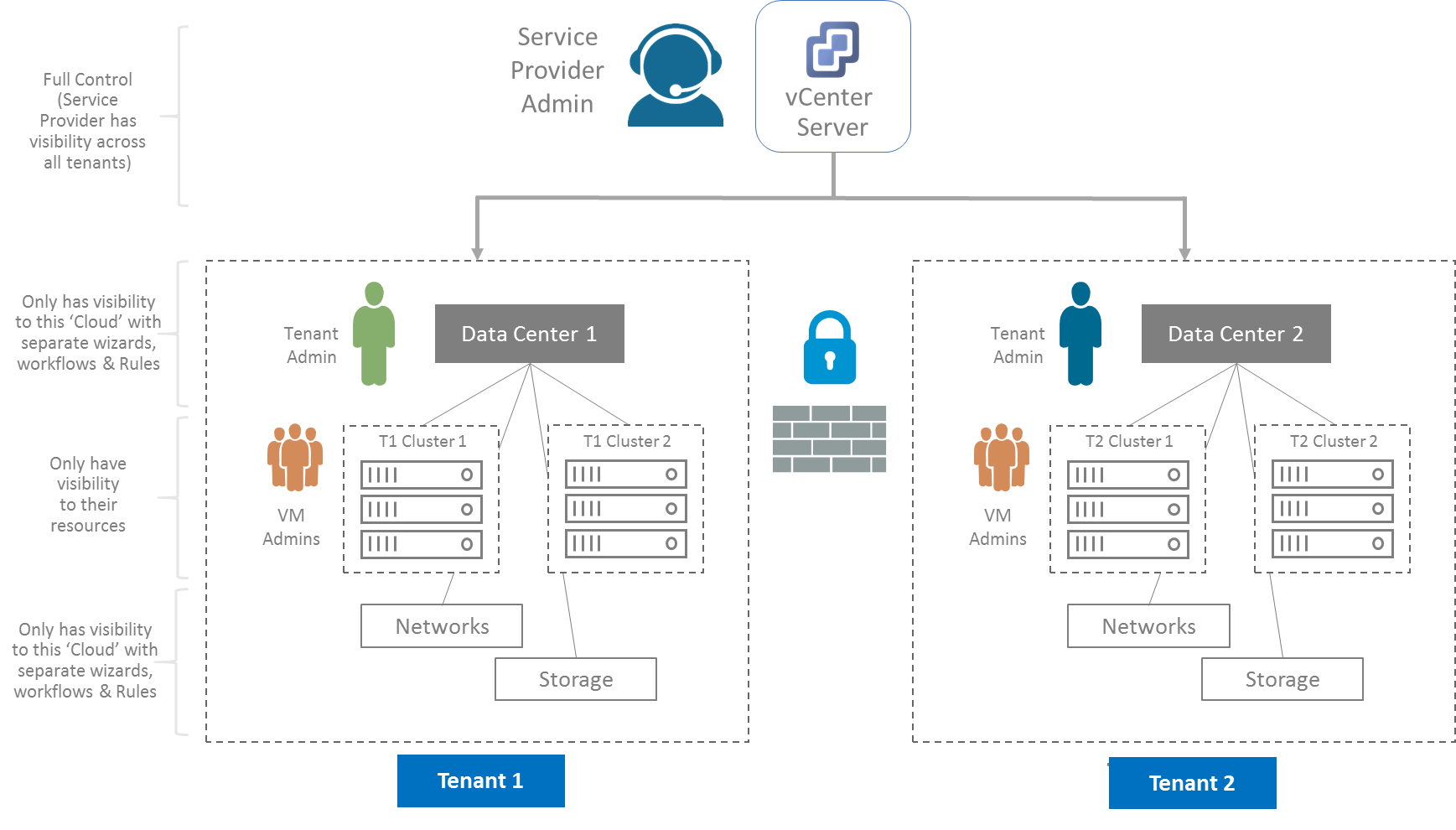
Which subset of access control rules on DB can ensure confidentiality... | Download Scientific Diagram
Rule-based access control blue gradient concept icon. Security management abstract idea thin line illustration. Authorized employees. Isolated outline drawing 24053135 Vector Art at Vecteezy
![PDF] Runtime support for rule-based access-control evaluation through model-transformation | Semantic Scholar PDF] Runtime support for rule-based access-control evaluation through model-transformation | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7094b8b115bc152fd65b11366cbe971d51cc4663/3-Figure2-1.png)
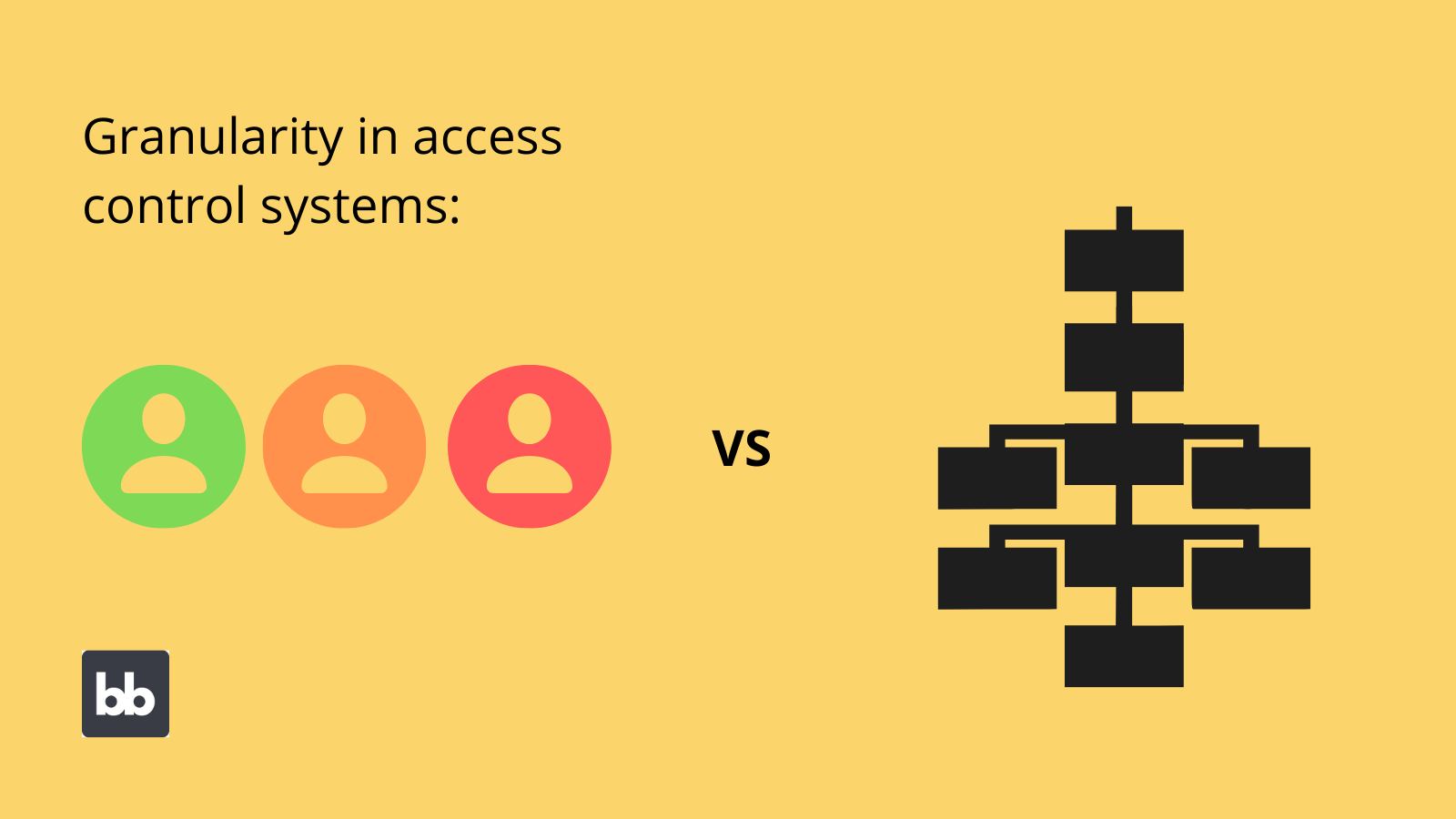



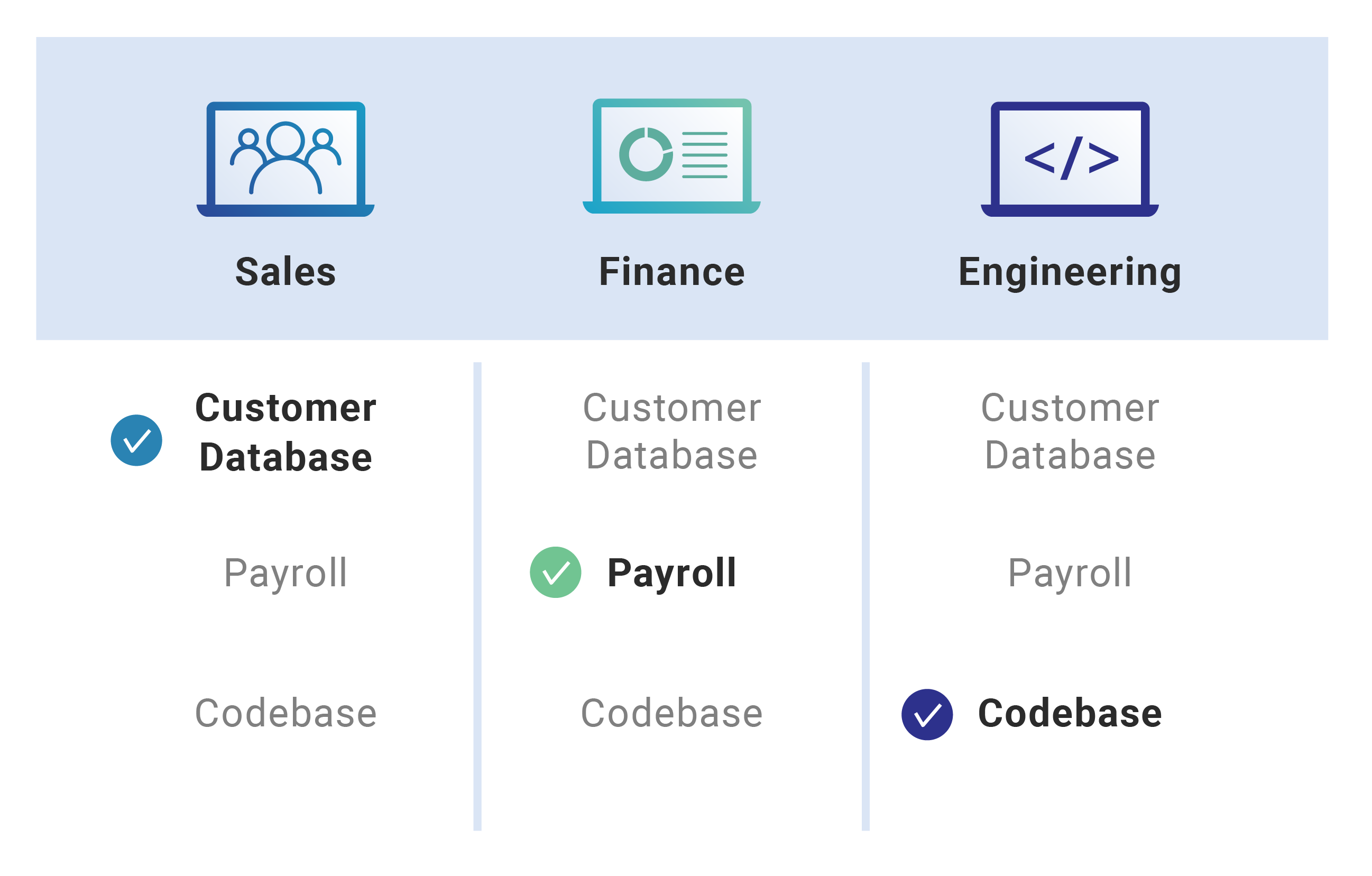


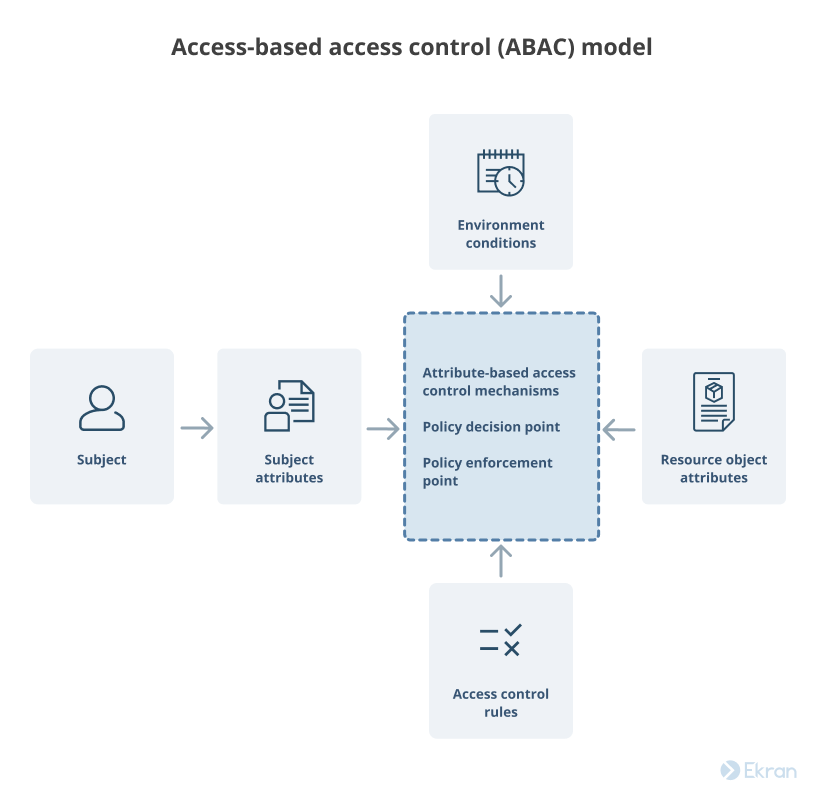
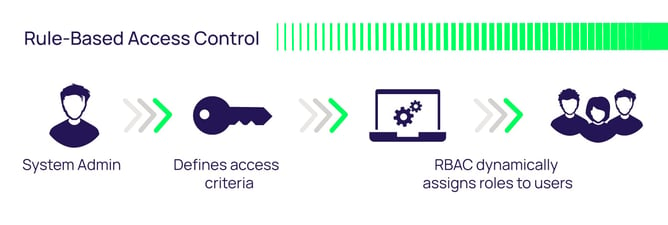
![PDF] Design and Application of Rule Based Access Control Policies | Semantic Scholar PDF] Design and Application of Rule Based Access Control Policies | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7d483c6b457f0263c18b821782773ea05f812f52/4-Figure2-1.png)